Configuring ACP to verify the client mTLS authentication
Instructions on configuring ACP to verify the client mTLS authentication
If a client or a server has the mTLS token endpoint authentication method enabled, you can configure your workspace to use root CA (certification authority) certificates instead of system root certificates for tls_client_auth purposes.
Prerequisites
You have login credentials to ACP.
Select workspace
-
In your browser, navigate to ACP and log in with your credentials.
-
From Workspace Directory, select a workspace that you want to enter.
Navigate to auth settings
-
In the workspace, select Settings from the sidebar.
-
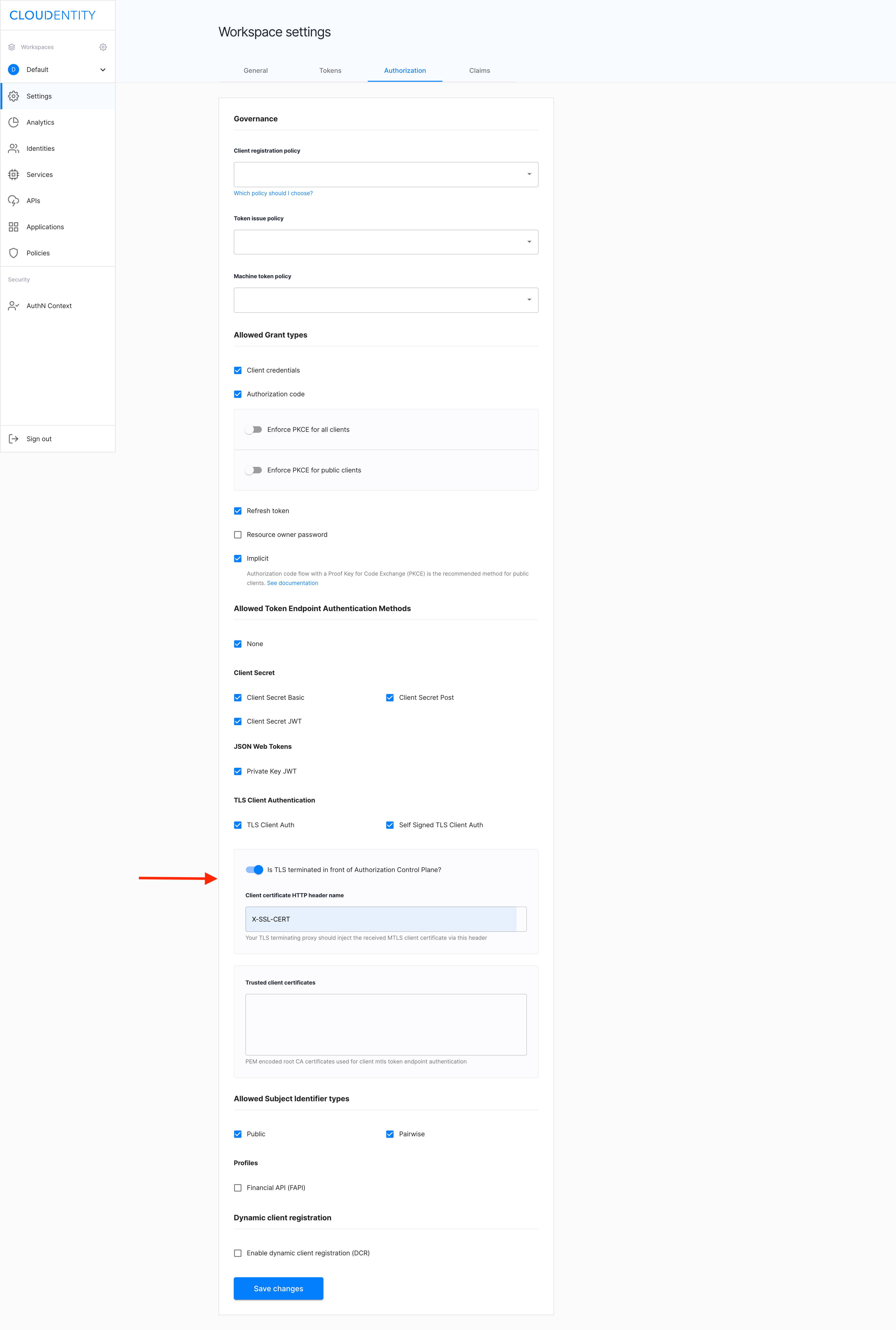
From the Workspace Settings view, select the Authorization tab.
Enable Root CAs
-
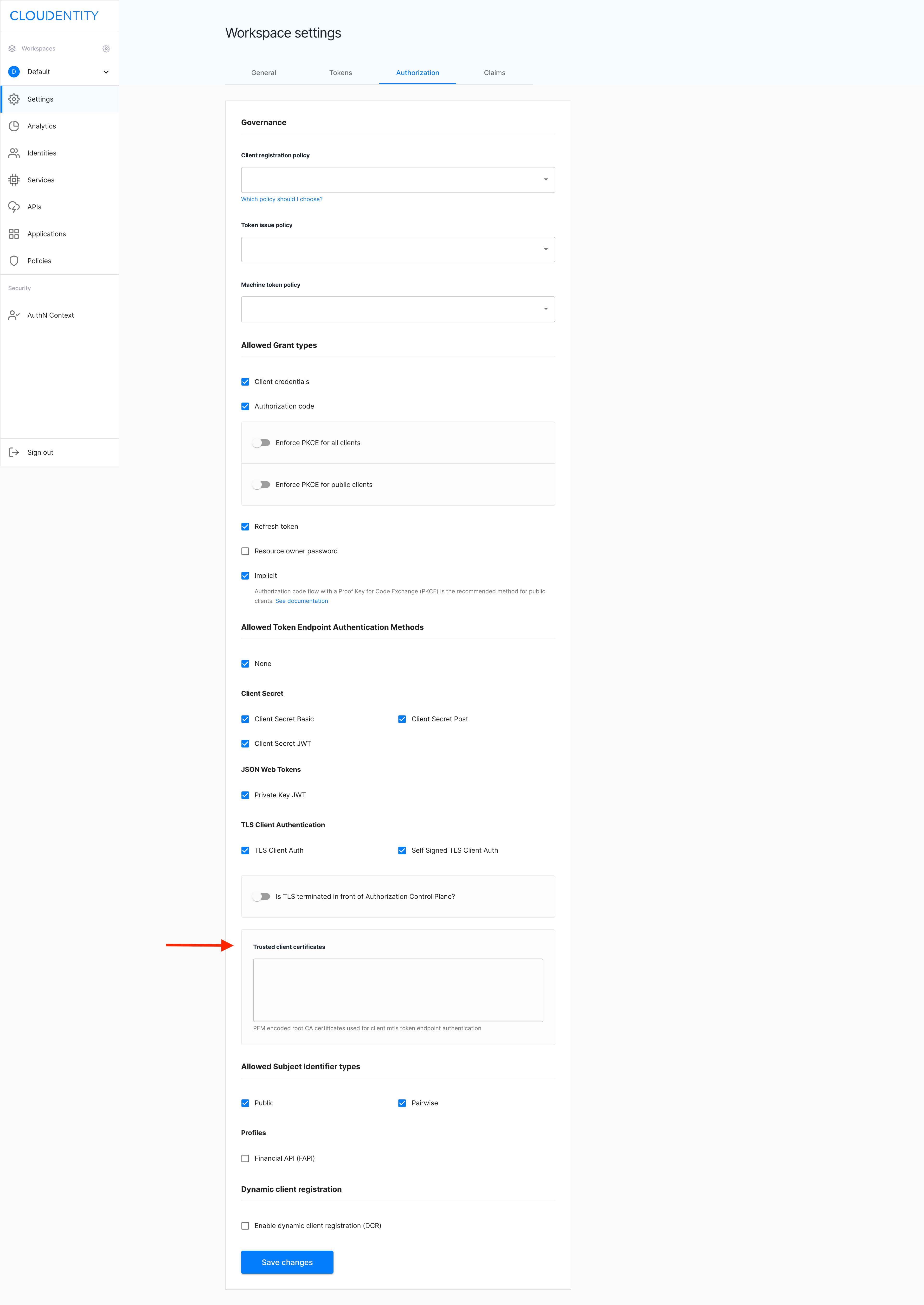
In the Authorization tab, navigate to the Trusted client certificates section.
-
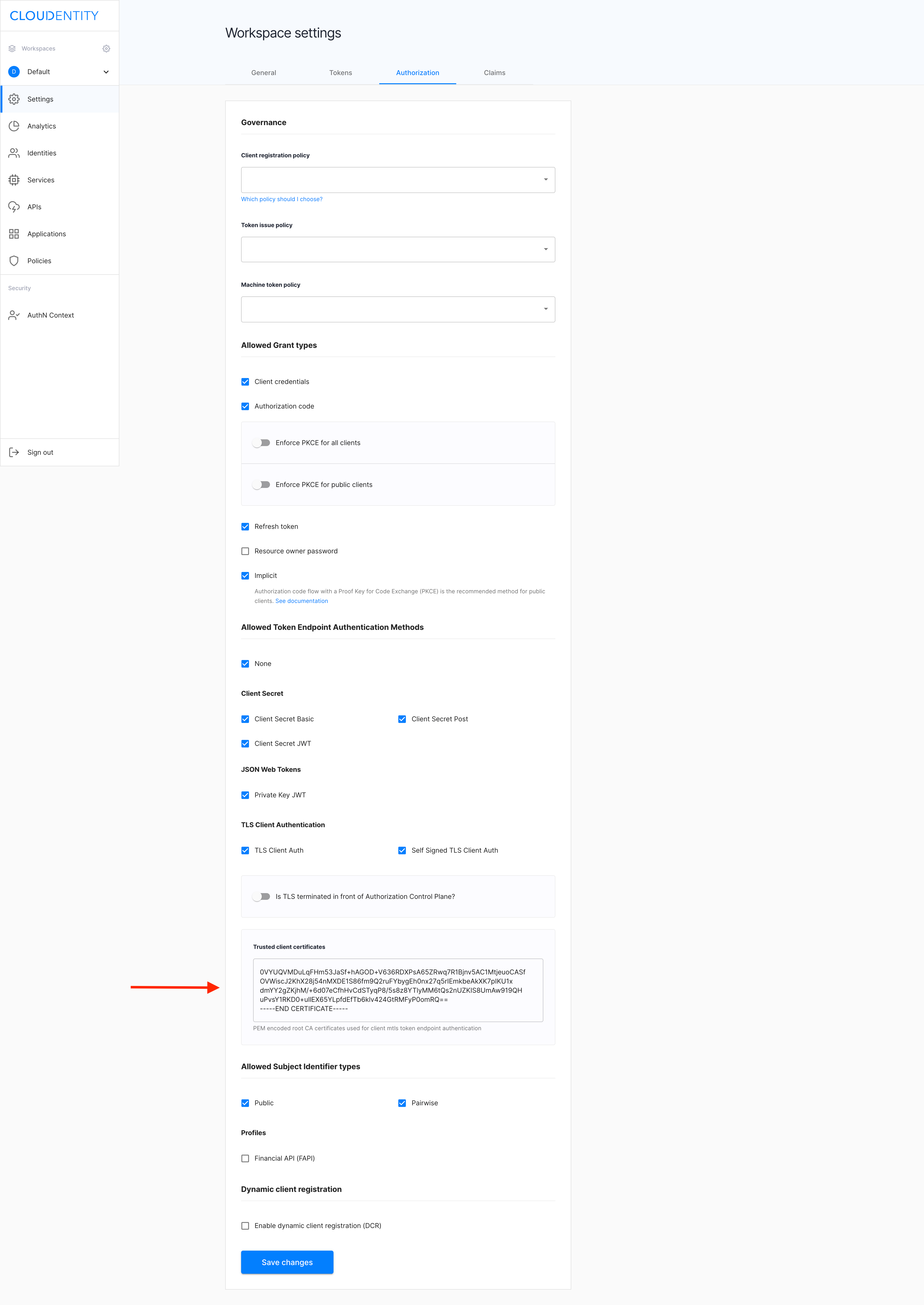
Enter root CA certificates into the Root CAs field and select Save changes.
Read a client certificate from the header
If your ACP implementation includes a load balancer, you can read a client certificate from the header.
Enable this function by configuring the load balancer so that it injects the certificate from the client request into ACP as a header with the name specified.
Select toggle switch Is TLS terminated in front of Authorization Control Plane? and enter the header name into the Client certificate HTTP header name.
Result
For clients/servers with the tls_client_auth method enabled, root CA certificates are used instead of system root certificates.