ACP authorization code grant flow
Learn what an authorization code grant is and what its process is. Find out what type of applications can use the authorization code grant flow in a safe and secure manner.
In a nutshell
The ACP OAuth authorization code grant flow type can be used for obtaining access tokens, refresh tokens, or OIDC tokens. It can be used by confidential clients, for example, web applications, that are able to store their authorization code safely to exchange it for a token later on.
The authorization code is a temporary code that proves to ACP that the client requesting for a token is authorized to do so. This code is provided to the client by ACP after the user has successfully provided their consent.
This grant flow is designed to be used by applications that have a back-end parts. It is not possible to use the authorization code grant flow by a single-page application unless it uses the Proof Key of Code Exchange (PKCE).
Prerequisites
To use the ACP authorization code grant flow type, the client must match the following criteria:
-
It must be able to interact with the resource owner’s user-agent, for example, a web browser.
-
It must be capable of receiving incoming requests (via redirection) from the authorization server.
Flow in depth
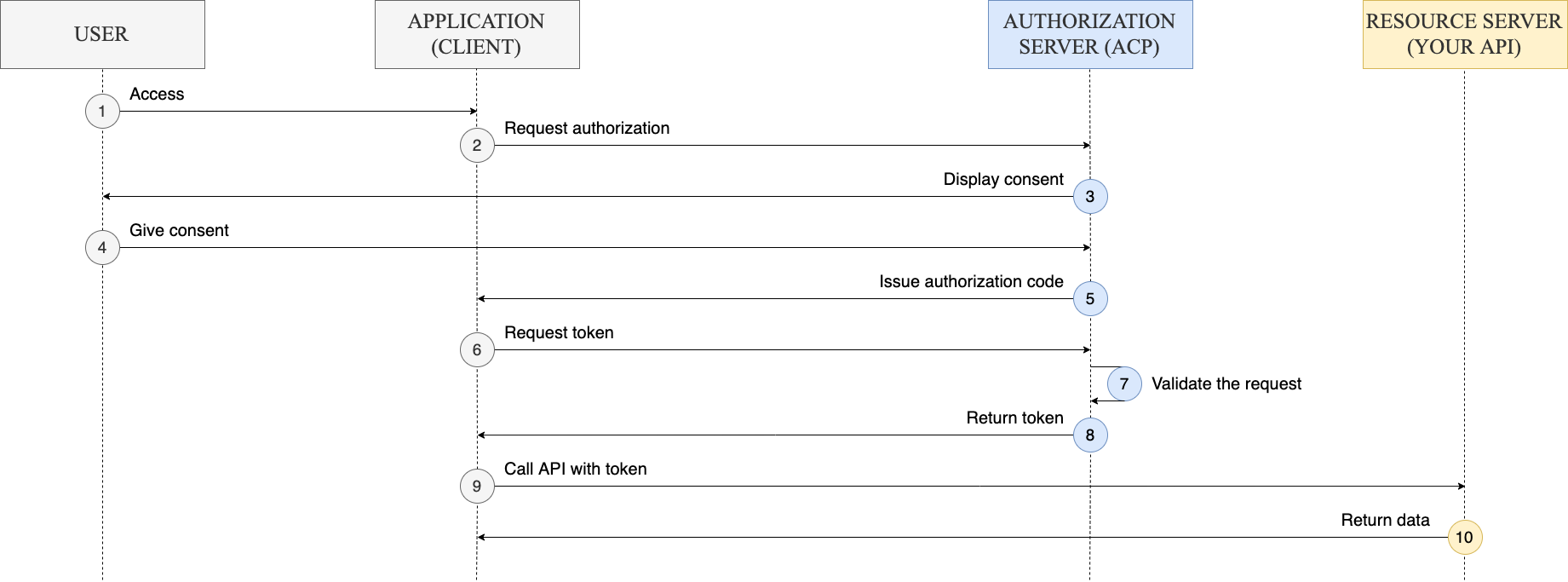
The example flow diagram above illustrates the interactions that occur in the ACP OAuth authorization code grant flow.
-
A user tries to access the application (the client).
-
The client redirects a user to the authorize endpoint.
Note
The client must inform ACP of its desired grant type by using the
response_typeparameter. For the authorization code grant flow type, the value of theresponse_typeparameter must becode. -
ACP authenticates the user and displays a consent screen if there is an authorization scope to be granted.
Note
ACP does not display consent screen when there is no authorization scope to be granted.
-
The user gives their consent.
-
ACP issues an authorization code.
Note
After ACP generates the authorization code, it is redirected to the redirection endpoint configured for the registered client. If no redirection endpoint was specified during the client registration (it is not recommended), it can be provided using the
redirect_uriparameter in the request to theauthorizeendpoint. -
The client requests authentication to the token endpoint using authorization code provided in the previous step.
Read more
To learn more about token endpoint authentication methods, see the client authentication documentation.
-
ACP validates the request.
-
ACP returns the token.
-
The client requests protected resources from the resource server and submits the token it received in the previous step.
-
The resource server validates the token and responds with requested resources.