Prerequisites for deploying and protecting services
This article provides the prerequisites for deploying and protecting services both with the HTTP and gRPC methods.
Install the Kubernetes cluster with Istio
Prerequisites
-
Kubernetes version 1.14 or subsequent.
-
Istio version 1.9 or subsequent.
Procedure
Note
As an alternative to this procedure, you can install Istio using the ACP on k8s repository which provides simple deployment commands you can use out of the box.
-
Set up a Kubernetes cluster locally using kind.
GO111MODULE="on" go get sigs.k8s.io/kind@v0.9.0 && kind create cluster -
Install Istio.
curl -L https://istio.io/downloadIstio | sh - cd istio-1.8.2 export PATH=$PWD/bin:$PATH istioctl install --set profile=demo -y kubectl label namespace default istio-injection=enabledResult
Istio is installed, added to PATH, and Istio injection is enabled on the default namespace.
✔ Istio core installed ✔ Istiod installed ✔ Egress gateways installed ✔ Ingress gateways installed ✔ Installation complete -
Define the authorizer
-
Edit the mesh config with the following command:
kubectl edit configmap istio -n istio-system -
Define ACP authorizer using extension providers, for example:
data: mesh: |- extensionProviders: - name: "acp-authorizer" envoyExtAuthzGrpc: service: "istio-authorizer.acp-system.svc.cluster.local" port: "9001" -
Restart Istio to apply the changes:
kubectl rollout restart deployment/istiod -n istio-system
-
Create the Istio gateway
-
In the workspace, select APIs from the sidebar.
-
Select the GATEWAYS tab.
-
Select ADD GATEWAY.
-
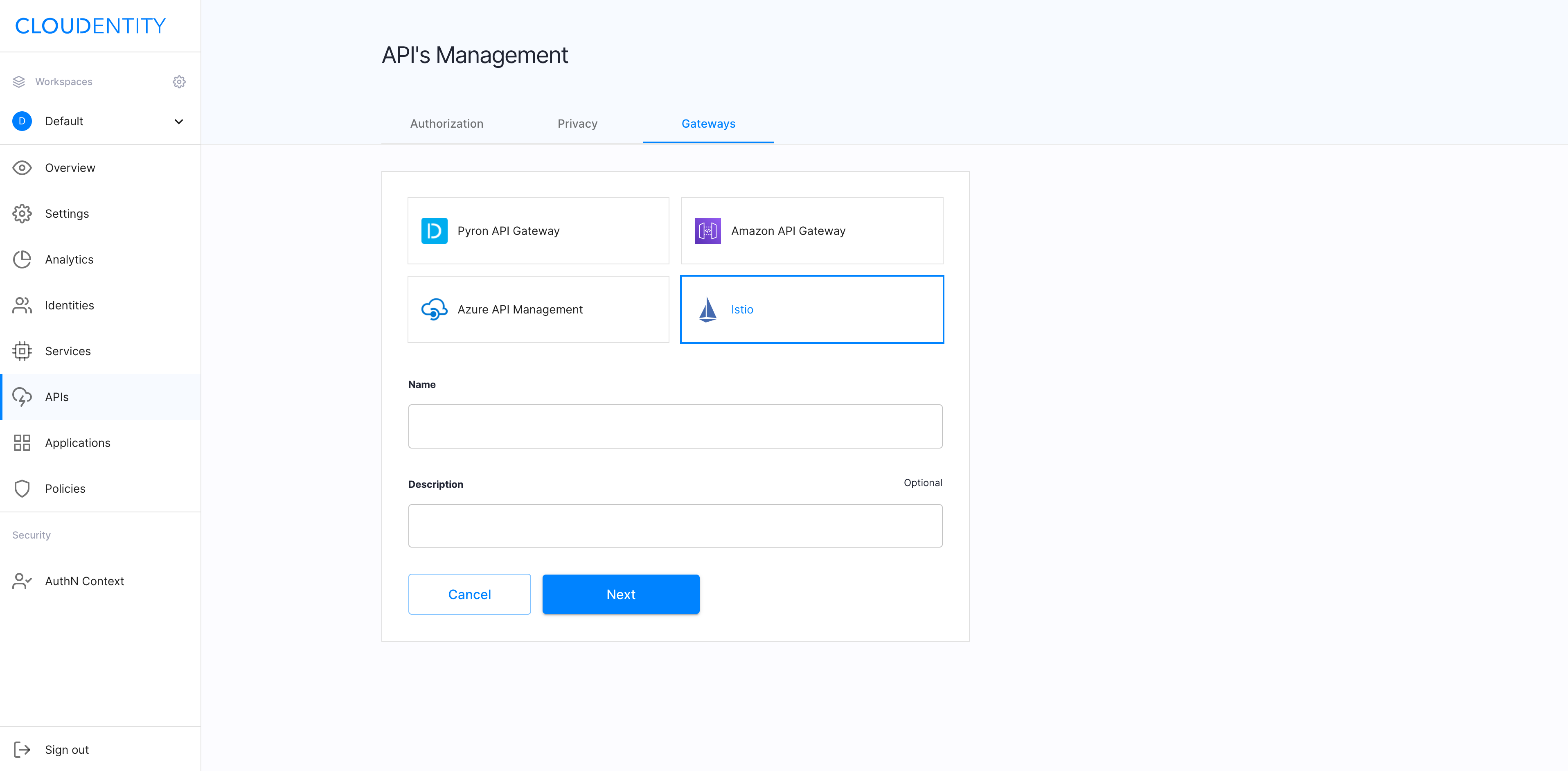
Select Istio, enter the name and the description for your gateway, and select NEXT.
-
In the Gateway Management view, go to the QUICK START tab and proceed as follows:
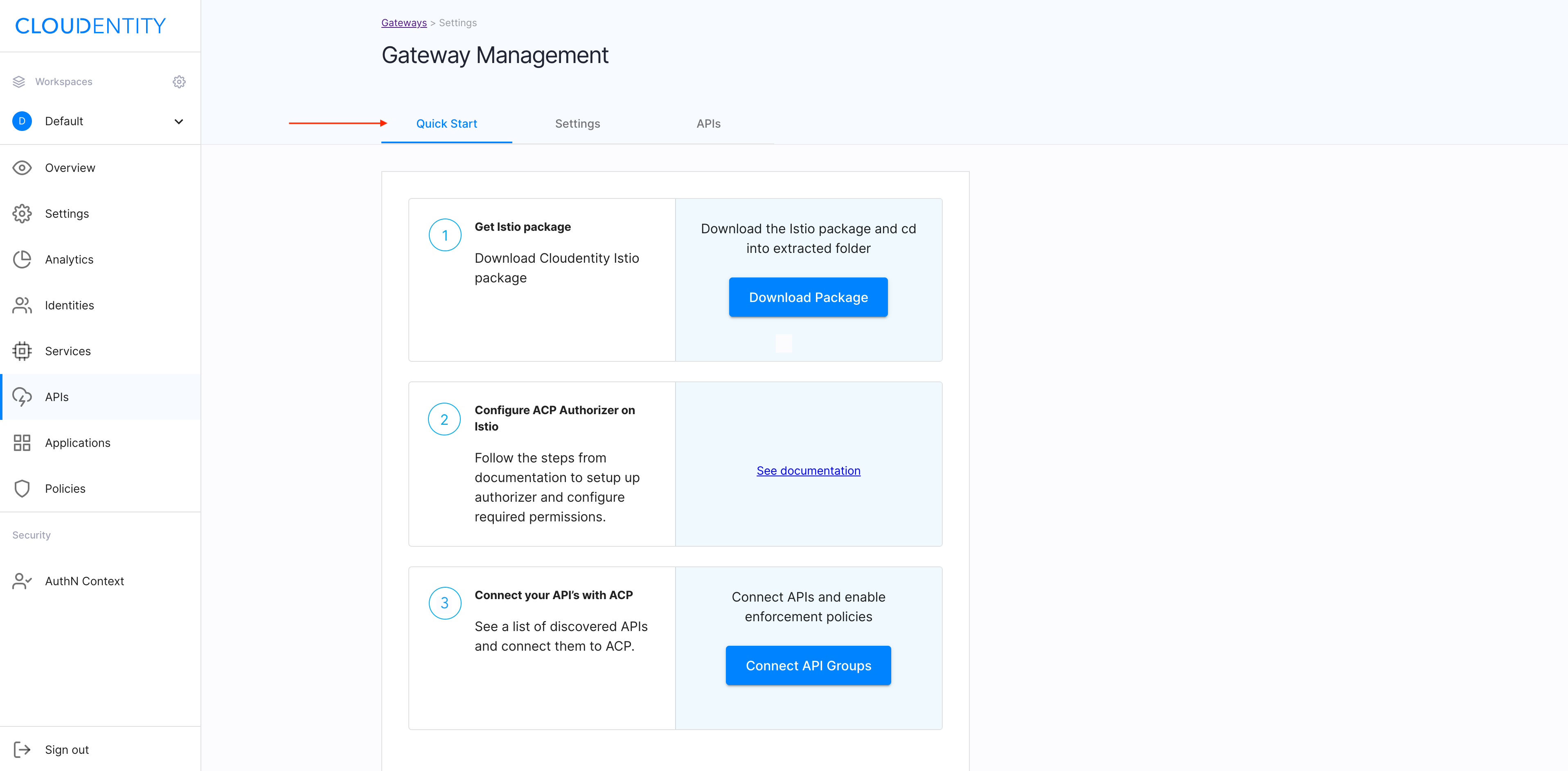
-
Select Download Package to download the zipped Istio Authorizer package. Unzip the package locally and enter the extracted folder.
Note
The package includes
-
manifest.yamllisting API details -
kustomization.yamldefining resources and secret generator inputs. -
parse-body.yamlthat can be used to indicate that the request body is going to be parsed. You can use JSON validators to check the request body assertions.
-
-
To deploy Istio Authorizer, execute
kubectl apply -k .Result
Istio Authorizer scans deployments in configured namespaces and funnels information about discovered APIs to ACP. Note that if you didn’t deploy any service yet, there’s nothing to discover. To quickly deploy a sample HTTP/gPRC service, follow:
-
Back in the ACP administrator portal (Gateway Management > QUICK START), select CONNECT API GROUPS to connect APIs and enable enforcement policies.
Result
The predefined set of API groups is imported and displayed in the APIs tab of the Gateway Management view. The API groups are ready to be connected to services (unless you selected the automatic binding option when creating the gateway in ACP).
-
Related articles
Having created a k8s cluster with Istio, you can